Cybersecurity Maturity Model Certification is a program initiated by the United States Department of Defense (DoD) in order to measure their defense contractors’ capabilities, readiness, and sophistication in the area of cybersecurity. At a high level, the framework is a collection of processes, other frameworks, and inputs from existing cybersecurity standards such as NIST, FAR, and DFARS.
At a tactical level, the primary goal of the certification is to improve the surety and security of Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) that is in the possession and use of their federal contractors.
CMMC assesses suppliers’ security programs and ensures that those suppliers have sufficient systems in place to protect any CUI that resides on their networks. It’s designed to reduce vulnerabilities in the supply chain, protect DoD information from breaches, and improve overall cybersecurity practices.
Recognizing that there needed to be more structure than the self-certification of compliance with NIST SP 800-171, the Department of Defense began developing what would become the Cybersecurity Maturity Model Certification (CMMC).
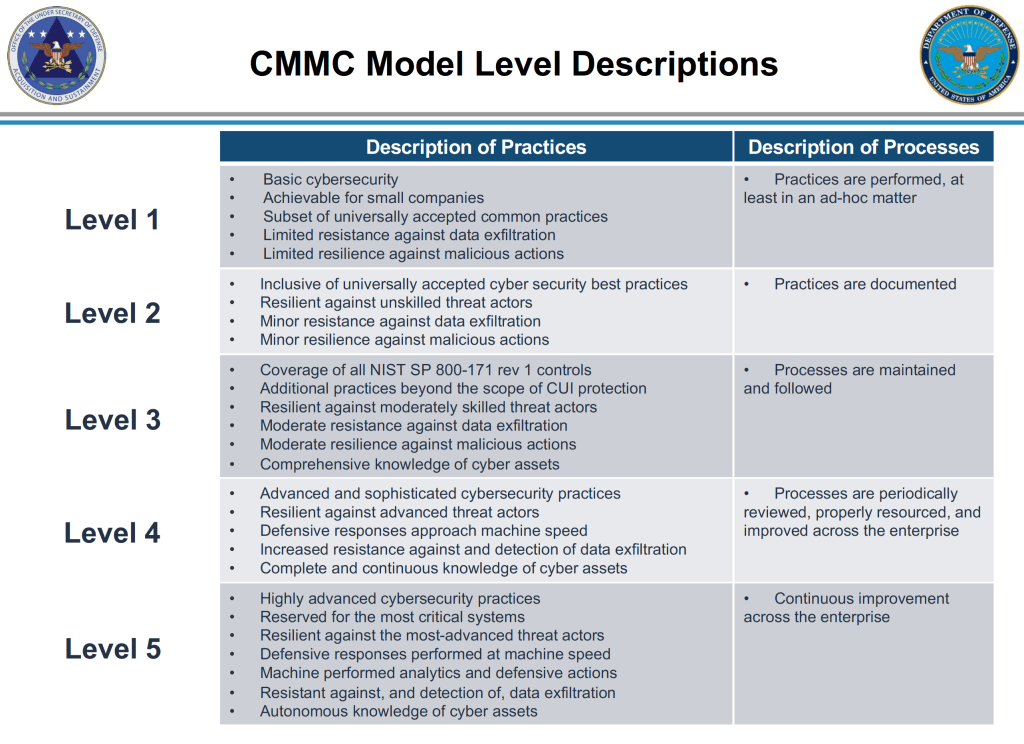
The CMMC is an amalgam of multiple frameworks and standards including NIST SP 800-171, the NIST Cybersecurity Framework, and others. Developed by the DoD in conjunction with academia, the CMMC leverages a combination of practices, controls, and processes that gauge the maturity level of a given practice. Recognizing that not all contractors need to have the same cybersecurity program maturity as a prime, the DoD will include which of the five maturity tiers a given contract will require at the time of a request of information. A contractor’s tier score will be assessed and audited via third-party CMMC assessments and auditors. These third-party assessment organizations will be appointed by the CMMC Accreditation Board and the CMMC certification for a given tier will last for three years.
CMMC Level 3
Level 3 focuses on the protection of CUI and encompasses all of the security requirements specified in NIST SP 800-171 as well as 20 additional practices to mitigate threats. Any contractor with a DFARS clause in their contract will need to at least meet Level 3 requirements.
CMMC Level 3 Overview
There are 130 controls that make up CMMC Level 3, which encompasses the CMMC Level 1 & 2 controls. A CMMC Level 3 audit will cover 100% of the 110 NIST SP 800-171 CUI controls and adds an additional 20 controls from various sources.
The additional 20 non-NIST 800-171 controls are:
AM.3.036. Define procedures for the handling of CUI data.
AU.3.048. Collect audit logs into a central repository.
AU.2.044. Review audit logs.
IR.2.093. Detect and report events.
IR.2.094. Analyze and triage events to support event resolution and incident declaration.
IR.2.095. Develop and implement responses to declared incidents according to pre-defined procedures.
IR.2.097. Perform root cause analysis on incidents to determine underlying causes.
RE.2.137. Regularly perform and test data back-ups.
RE.3.139. Regularly perform complete and comprehensive data back-ups and store them off-site and offline.
RM.3.144. Periodically perform risk assessments to identify and prioritize risks according to the defined risk categories, risk sources, and risk measurement criteria.
RM.3.146. Develop and implement risk mitigation plans.
RM.3.147. Manage non-vendor-supported products (e.g., end of life) separately and restrict as necessary to reduce risk.
CA.3.162. Employ code reviews of enterprise software developed for internal use to identify areas of concern that require additional improvements.
SA.3.169. Receive and respond to cyber threat intelligence from information sharing forums and sources and communicate to stakeholders.
SC.2.179. Use encrypted sessions for the management of network devices.
SC.3.192. Implement Domain Name System (DNS) filtering services.
SC.3.193. Implement a policy restricting the publication of CUI on publicly accessible websites (e.g., Forums, LinkedIn, Facebook, Twitter, etc.).
SI.3.218. Employ spam protection mechanisms at information system access entry and exit points.
SI.3.219. Implement DNS or asymmetric cryptography email protections.
SI.3.220. Utilize email sandboxing to detect or block potentially malicious email attachments.
Aviation Instrument Technologies, Inc. is CMMC level 3 Certified.